Net Switzerland in Danger
Switzerland is famous for cheese, chocolate, numbered bank accounts, and for being a neutral country, which probably enabled those numbered accounts in the first place. High worth individuals felt comfortable stashing their well- or ill-gotten gains because they knew Switzerland wasn’t likely to kowtow to law enforcers or snooping governments from other countries – they were neutral.
Up until the present moment, the Internet has been a neutral country; if you have enough money for an Internet connection, your traffic is accepted and delivered to its destination just like anyone else’s. The product of a democratic nation, the Internet has been the ultimate democracy. People coming to the StratVantage site enjoy the same speed and priority as people going to Yahoo, Google, Microsoft, or the other mega-sites. And that’s the way we like it.
Burgeoning businesses such as MySpace, Facebook, Friendster, and YouTube have been able to catch on and grow with only the relatively minor growing pains of having to pay more to their Internet Service Providers due to an increase in traffic.
But there are folks, not coincidentally folks in the Internet backbone business, who would like higher volume sites to pay more for the privilege of receiving users’ traffic.
One
of the first indications of the change in attitude from the semi-altruistic
policy of “We’ll carry anyone’s traffic, and anyone will carry ours” came last
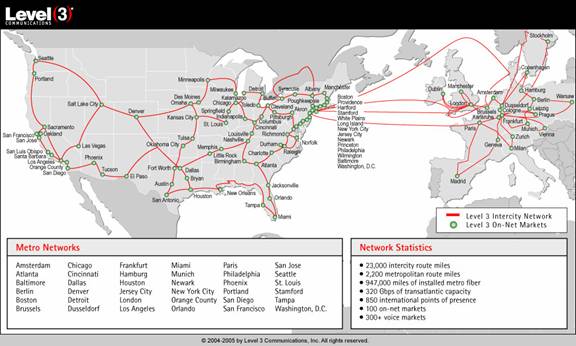
fall when Level 3 Communications refused
to carry the traffic of another Internet infrastructure provider, Cogent Communications.
Level 3 shut down the connection between itself and Cogent, affecting many of Cogent’s
9,500 customers, including Time Warner Cable, Harvard, Boston College, and MIT,
isolating them from key areas of the Internet.
According
to a Network World article
at the time:
Peering is mutually advantageous when both partners
exchange similar traffic volumes, but Level 3 says it was carrying the bulk of
the traffic in its deal with Cogent. "The larger company ends up
disadvantaged because it ends up providing essentially free capacity,"
said Level 3 spokeswoman Jennifer Daumler. "In Cogent's case, we
determined that the arrangement was not reasonable or commercially
viable."
Cogent CEO Dave Schaeffer disputes Level 3's
characterization and says the dropped peering arrangement is really Level 3's
attempt at playing hardball with a rival that has been undercutting it on
pricing.
"The root cause of this is Level 3's strong
desire to pressure Cogent into raising our prices," Schaeffer said.
"They have been very vocal and very upset at our gain in market share and
our pricing policy."
Because the Internet is highly redundant, even when a peering relationship ends, traffic may still go through, using roundabout, slower routes, but some traffic won’t be delivered. Thus peering ensures quicker delivery of traffic and a more-responsive Internet. (Incidentally, if you’re interested in an up-to-the-minute snapshot of how well the Internet is working, check out the Internet Health Report.)
Cogent has had similar fights with other peers, notably AOL and France Telecom, both of which ended peering agreements with Cogent. And this was not the first dispute over peering that we’ve seen. In 2001, a similar contract dispute led Cable & Wireless to cut off its connection to PSINet, one of the oldest Net backbone companies.
The Internet was built on this very important idea: Big infrastructure providers, whose long, high-speed communications lines crisscross the country and the world, would enter into peering agreements with other providers, thus enabling both peers to hand off traffic in order to get it delivered to its ultimate destination.
 There
would be no Internet today if these providers had not developed this system of
traffic routing. If there were no mutual peering agreements, each network would
have to negotiate with all other networks and charge them for handling, for
example, East Coast traffic on one network destined for Google’s servers in San
Francisco, on another network.
There
would be no Internet today if these providers had not developed this system of
traffic routing. If there were no mutual peering agreements, each network would
have to negotiate with all other networks and charge them for handling, for
example, East Coast traffic on one network destined for Google’s servers in San
Francisco, on another network.
While providers might be able to argue that they would have made more money by charging for peering connections, adding a huge bureaucratic system of charge backs and trades would make the Internet less free (and more expensive) and less efficient.
It turns out many of these Internet backbone providers aren’t making money – both Level 3 and Cogent are bleeding cash, and Cogent is undercutting everyone’s prices. So it’s only natural that they are trying to increase their revenue. And their latest idea is a really bad one for neutrality, democracy, and the little guy.
Backbone providers plan to start shaking down huge Websites for protection money (Youse know, Mr. Google, it would be a real shame if sumptin’ was to happen to your traffic from my network, know whad I mean?) has raised a stink among the digerati (Web originator Tim Berners-Lee) and, alas, our elected representatives, who never met a hyperbolic name for a bill they didn’t like (Internet Freedom Preservation Act, Internet Non-Discrimination Act of 2006, Net Neutrality bill, Communications Opportunity, Promotion, and Enhancement Act of 2006, Communications, Consumer's Choice, and Broadband Deployment Act of 2006).
Although
they evidently have gotten the buzzword for the controversy – Net
Neutrality – Congress still doesn’t seem to get that the Internet, being a
worldwide phenomenon, is not totally under their control. While US legislation
can affect US backbone providers, it obviously cannot coerce providers
throughout the world. The relevant section of the most popular bill, the Snowe-Dorgan-Inouye
Internet Freedom Preservation Act, goes thusly:
(4) [Providers must] enable any content,
application, or service made available via the Internet to be offered,
provided, or posted on a basis that-
(A) is reasonable
and nondiscriminatory, including with respect to quality of service, access, speed,
and bandwidth;
(B) is at least
equivalent to the access, speed, quality of service, and bandwidth that such
broadband service provider offers to affiliated content, applications, or
services made available via the public Internet into the network of such broadband
service provider; and
(C) does not impose a
charge on the basis of the type of content, applications, or services made
available via the Internet into the network of such broadband service provider;
(5) [Providers must] only prioritize content,
applications, or services accessed by a user that is made available via the
Internet within the network of such broadband service provider based on the
type of content, applications, or services and the level of service purchased by
the user, without charge for such prioritization;
and
(6) [Providers must] not install or utilize network
features, functions, or capabilities that impede or hinder compliance with this
section.
What this section says is, Internet providers can’t discriminate against its best customers. This hardly seems to be the type of thing that should be legislated. It seems more like a rule of good business. Next Congress will declare that airlines can’t charge more for tickets bought close to the departure date, which also effectively discriminates against their best customers – business travelers. Wait a minute. That actually might not be a bad idea!
Alert
SNS Reader Larry Kuhn sums up his attitude toward Net Neutrality enforced
through US laws like this:
Personally, although I know I’m living in fantasy
world, I’d prefer if we could maintain net neutrality without laws to mandate
it. These types of legislated technology mandate, although they begin with
the noblest of intents, always have a way of inspiring odd and unexpected
corporate profiteering and bureaucratic inefficiency that will look very
foolish many years down the road when the technology changes enough to disrupt
the assumptions that the laws are based on.
I would liken the whole net neutrality situation to
the way wireless spectrum is handled today. The entire structure is
predicated on the technology of the earliest days of analog radio technology,
and it completely stifles the use of spread spectrum and other technologies
that could deliver more capability more cheaply than what we are now legally
allowed.
I agree with Larry. We can’t rely on Congress solving a problem now without creating another problem later.
Legislating Net Neutrality is bad enough, but the act also proposes another, possibly more deeply flawed, technical solution. It prevents providers from establishing different classes of network traffic (like enabling better Quality of Service (QoS) for voice and video.) QoS guarantees are actually one of the biggest deficiencies in the current Internet. Packets are packets, and all are routed with the same priority. Those who want to provide voice or video services on the Internet struggle with this fact.
So why should you care? If the bittorrent packets of last night’s episode of Desperate Housewives are delayed a few milliseconds on their way to you, it might not matter too much to you. But if the packets that make up live video or a phone call are delayed, the quality dramatically suffers and you will definitely not be happy.
Inserting QoS concepts into the way Internet traffic is routed may be required for it to take the next leap, and become a reliable, efficient delivery pipe for all kinds of on-demand, real-time content.
Congress would be wise to stay out of technical and business decisions like these and let the market take care of it. That’s what happened with the Level 3 case: Users got up in arms about the disruption in service and Level 3 had to back down. Setting a precedent of regulating the Internet could be the mythical slippery slope that gives legislators the idea that they can control not only how the Internet is put together, but ultimately – like China – control the kind of content that moves over it.
If a single Internet provider started to charge large Websites more for bandwidth or to guarantee preferred delivery, they’d be cutting their own throats. If the whole industry colluded, with a nod and a wink, and all started to do it, the government could prosecute under existing anti-trust laws. Even if that was ineffective, smaller players would inevitably take the initiative to fill the void, perhaps using the tens of thousands of miles of dark fiber already in the ground. (At one point, Level 3 had 16,000 miles of intercity dark fiber capacity available for sale.)
There’s an old saying about the Internet coined by John Gilmore, one of the co-founders of the Electronic Frontier Foundation: “The Internet interprets censorship as damage and routes around it.” In this case, the Internet would interpret the obstruction posed by higher rates for popular sites as damage, and route around that.
There’s also little likelihood, in my view, that the huge companies who depend on the Internet for their livelihood, including Google, Yahoo, and Microsoft (try downloading Microsoft’s patch-of-the-month over a dial-up connection), would sit idly by while they were gouged. Chances are good they’d band together and get into the telecommunications business. (Google’s already doing that as a partner in the citywide San Francisco wireless project and has expressed interest in hiring a dark fiber employee who would be responsible for “Identification, selection, and negotiation of dark fiber contracts both in metropolitan areas and over long distances as part of development of a global backbone network.”)
So
I don’t think legislation is the answer, but Internet users should be worried
nonetheless. Think of how your business would be affected if your Website (and
email) were relegated to a low-bandwidth, backwater ghetto of the Internet. Let
your elected representatives know what you think on the subject of Internet
neutrality, and hope they get a clue.
Briefly Noted
- Shameless Self-Promotion
Dept.: As if I don’t have enough Websites, I just released www.YourWhitePaper.com, which,
oddly enough, is all about how I can write a technical white paper to help
you market your products or services.
I’ve added a bunch of stuff that didn’t make it into SNS to the Raw File, a collection of such tidbits. It’s now over half a meg, so I split the page into two parts.
I’m republishing SNS on a couple of other services now, including Gather, and I’ve changed the StratVantage Stratlets hosting to use Blogspot.
I was interviewed for ManagementFirst’s Feature of the Month and got to toot my horn for a bit.
The WiMAX Guys’ main business is new installs for people who want to set up wireless hotspots such as hotels, warehouses, apartment buildings, and office buildings or hotzones that cover cities. We also sell a knowledge-based Web portal called the MAX K-Base. Check out our main Website at www.TheWiMAXGuys.com.
The first chapter of my wife’s novel, Knowing What You Know Today is up on her Website. The rest of the book costs money – now at a new lower price! – but it’s well worth it, believe you me. Check it out at www.debellsworth.com. She’s also put up a new site, www.empathysymbol.com to publicize the empathy symbol she designed back in college.
Many issues ago I debuted SNS Begware, an opportunity for you, gentle reader, to express your appreciation by tipping your server via PayPal. See the sidebar for more info. Total in the kitty so far: $111.48.
And now that I’m partnered with one of the largest advertisers on the planet, Google, that should be kicking in serious coin to the StratVantage coffers. Let’s see. The current total is: $89.84. Great. BTW, I am informed that I can’t ask you to read this issue on the Web and click on the ads due to Google’s terms of service. So don’t. You can, however, shop at Amazon, pay nothing additional, and send a spiff to me.
- FISH of the Day: The Forwarded Internet Serial Humor of the Day today comes from Alert SNS Reader Doug Laney of Evalubase Research. And they call it the Weaker Sex . . .
THE NEXT SURVIVOR SERIES
Six married men will be dropped on an island with one car and 3 kids each for six weeks.
Each kid will play two sports and either take music or dance classes.
There is no fast food.
Each man must take care of his 3 kids; keep his assigned house clean, correct all homework, complete science projects, cook, do laundry, and pay a list of "pretend" bills with not enough money.
In addition, each man will have to budget in money for groceries each week.
Each man must remember the birthdays of all their friends and relatives, and send cards out on time.
Each man must also take each child to a doctor's appointment, a dentist appointment and a haircut appointment. He must make one unscheduled and inconvenient visit per child to the Urgent Care (weekend, evening, on a holiday or right when they're about to leave for vacation). He must also make cookies or cupcakes for a social function.
Each man will be responsible for decorating his own assigned house, planting flowers outside and keeping it presentable at all times.
The men will only have access to television when the kids are asleep and all chores are done.
There is only one TV between them, and a remote with dead batteries.
Each father will be required to know all of the words to every stupid song that comes on TV and the name of each and every character on cartoons.
The men must shave their legs, wear makeup daily, which they will apply to themselves either while driving or making three lunches.
Each man will have to make an Indian hut model with six toothpicks, a tortilla and one marker, and get a 4-year-old to eat a serving of peas.
Each man must adorn himself with jewelry, wear uncomfortable yet stylish shoes, keep his nails polished and eyebrows groomed. The men must try to get through each day without snot, spit-up or barf on their clothing.
During one of the six weeks, the men will have to endure severe abdominal cramps, back aches, and have extreme, unexplained mood swings but never once complain or slow down from other duties. They must try to explain what a tampon is for when the 6-yr old boy finds it in the purse.
They must attend weekly school meetings, church, and find time at least once to spend the afternoon at the park or a similar setting.
He will need to read a book and then pray with the children each night without falling asleep, and then feed them, dress them, brush their teeth and comb their hair each morning by 7. They must leave the home with no food on their face or clothes.
A test will be given at the end of the six weeks, and each father will be required to know all of the following information: each child's birthday, height, weight, shoe size, clothes size and doctor's name. Also the child's weight at birth, length, time of birth, and length of labor, each child's favorite color, middle name, favorite snack, favorite song, favorite drink, favorite toy, biggest fear and what they want to be when they grow up.
They must clean up after their sick children at 2:00 a.m. and then spend the remainder of the day tending to that child and waiting on them hand and foot until they are better.
They must have a loving, age appropriate reply to, "You're not the boss of me".
The kids vote them off the island based on performance. The last man wins only if...he still has enough energy to be intimate with his spouse at a moment's notice.
If the last man does win, he can play the game over and over and over again for the next 18-25 years...eventually earning the right to be called Mother!
- Join the Alert SNS Reader Group! You may have heard of a
concept called Web 2.0 (or even the more grandiose Web 3.0). Basically
it’s about adding to Web-based software the kind of interactive and
functionality we all take for granted in our installed software. It’s a
bunch more than that as well; Web 2.0 encompasses other concepts such as
Software as a Service (SaaS), Web services, and
Service Oriented Architecture (SOA). These are all fancy technologies that
enable an ordinary person – or at least an ordinary programmer person – to
pull together bits of functionality available on the Web to create
something new.
So to demonstrate the power of Web 2.0, I invite you to join the Alert SNS Reader Group. Just select Login to sign up.
- Hang on a Nanosec. Let Me Get That Info: Alert SNS Reader Ken Florian sent along a pointer to Mozy, the latest entry in the Will This Business Plan Fly? Sweepstakes. Mozy will remotely back up 20GB of your data for free. But that’s not what caught my eye on their site. Check out the following list of how long it takes to find information, based on where it is stored:
|
Data that lives here... |
...will take this long to access |
|
|
|
|
|
|
|
|
|
|
(Note that a nanosecond is 1 billionth of a second.)
- Cyber Best Practices: You may remember I wrote in a recent SNS about
what to do if your company is hit by a cyberattack.
Well the FBI coordinator of the local Infragard circulated a great document (1MB PDF)
called Best
Practices for Seizing Electronic Evidence. While you may not do
the seizing, knowing what law enforcement will be looking for if you want
them to catch the cybercriminals can really help,
so I’m hosting it on the StratVantage Website. There’s also an oldie but a goodie from 2001 Searching
and Seizing Computers and Obtaining Electronic Evidence in Criminal
Investigations (400KB PDF) in our security area.
- What if it was the “Microsoft iPod”? Alert
SNS Reader Larry Kuhn, a Microsoft employee, sent along this hilarious
YouTube short that envisions the packaging for the iPod
if it were a Microsoft rather than an Apple product. Truly hilarious, and
all too true.
YouTube
- Windows Can Drink: Obviously on a roll, Alert SNS Reader Larry
Kuhn went on to say, regarding an item in the previous SNS about Windows
turning 21, “At least now when it’s falling down drunk we don’t have to be
ashamed that it’s under the legal drinking age.”
- Free Wireless Everywhere? This issue’s second entry into the Will This Business Plan Fly?
Sweepstakes is M2Z Networks, which has a novel proposal for the
Federal Communications Commission (FCC). If the FCC will just grant M2Z
free wireless bandwidth everywhere, M2Z will provide free 512Kbps wireless
Internet everywhere. And that’s not all! M2Z proposes to kick back 5
percent of their revenues on faster wireless services to the FCC as, you
know, kind of a tip, a little something
for the effort. Now ordinarily I’d be laughing my butt off at such a
proposal. Indeed, most commentators point out that the FCC is in the
business of auctioning wireless bandwidth, not giving it away.
But check out who is behind M2Z: The venture is financed by heavyweight Sili Valley stars Kleiner Perkins Caufield & Byers, Charles River Ventures and Redpoint Ventures, and the company was started by the former head of the FCC's wireless bureau, John Muleta, and cable executive Milo Medin, who previously created AtHome Networks, one of the first cable-based data networks. So these guys aren’t crazy. You can read their 127-page FCC application (PDF) here.
MSN
- If You’ve
Made it This Far: I’m beginning to lose faith in the Alert SNS
Reader Nation. So far, no one has stepped up to try to join Alert SNS
Reader Ken Florian, the winner of our first Obscure Reference Contest, and
Alert SNS Reader Derek Dysart, our
second winner. Apparently, the third Obscure Reference Contest is
too hard for even the most accomplished Alert SNS googlesavant.
I find this to be a shame, but I’ll persist in my belief that somewhere
out there an Alert SNS Reader has the gumption, dogged tenacity, and
mastery of arcane rock and roll lore to solve the current puzzle.
I’m looking for the name of the album (and I’ll give you a hint: it’s only available in vinyl) (hint #2: one of the artists was in the Fugs) that featured an encounter between Johnny Pissoff and a guy with smooth hands as well as a Grateful Dead jam, and an ode to Captain Beefheart’s shoes. Extra points for including a link to the MP3 of the J. Pissoff epic.
Because it makes such a cool trophy, the prize is now two sticks of completely useless memory. So don’t let me down!
 All of the things that were written four years ago certainly apply today! I guess my main advice is, Don't Panic! In the computer forensics end of things, I'm not overly concerned or focused on what they are doing at the moment. My main focus is with what they've done.
All of the things that were written four years ago certainly apply today! I guess my main advice is, Don't Panic! In the computer forensics end of things, I'm not overly concerned or focused on what they are doing at the moment. My main focus is with what they've done.



 If You've Made it This Far: Alert SNS Reader Ken Florian was the winner of our first Obscure Reference Contest and was awarded not one, but two sticks of completely useless memory. Here's a picture of the coveted prize.
If You've Made it This Far: Alert SNS Reader Ken Florian was the winner of our first Obscure Reference Contest and was awarded not one, but two sticks of completely useless memory. Here's a picture of the coveted prize.